Crypto’s explosive growth, with Bitcoin currently priced at $110,786.00, continues to attract not just legitimate investors and professionals but also increasingly sophisticated cybercriminals. In 2025, North Korean hackers have escalated their efforts, targeting new and seasoned crypto workers alike with highly convincing job scams. If you’re entering the crypto workforce or even just networking in the space, understanding these evolving tactics is no longer optional, it’s essential for protecting your assets and identity.

How North Korean Hackers Are Weaponizing Fake Crypto Job Offers
Imagine this: you receive a message on LinkedIn from what appears to be a recruiter at Coinbase or Uniswap, inviting you to apply for an exciting new role. Everything checks out, the profile photo looks authentic, the company logo is there, and the job description matches your expertise. However, beneath this polished surface lies a dangerous trap.
According to recent reports from Reuters and BleepingComputer, North Korean hackers are saturating the industry with credible-sounding job offers as part of an ongoing campaign to steal digital assets. These attackers are leveraging AI-generated identities to pose as recruiters for top-tier crypto firms, making it increasingly difficult to distinguish between real opportunities and elaborate phishing attempts.
The Anatomy of a Crypto Job Scam in 2025
The latest wave of crypto job scams is disturbingly effective because it mimics legitimate recruitment processes down to the smallest detail. Here’s how these schemes typically unfold:
How North Korean Hackers Execute Crypto Job Scams
-
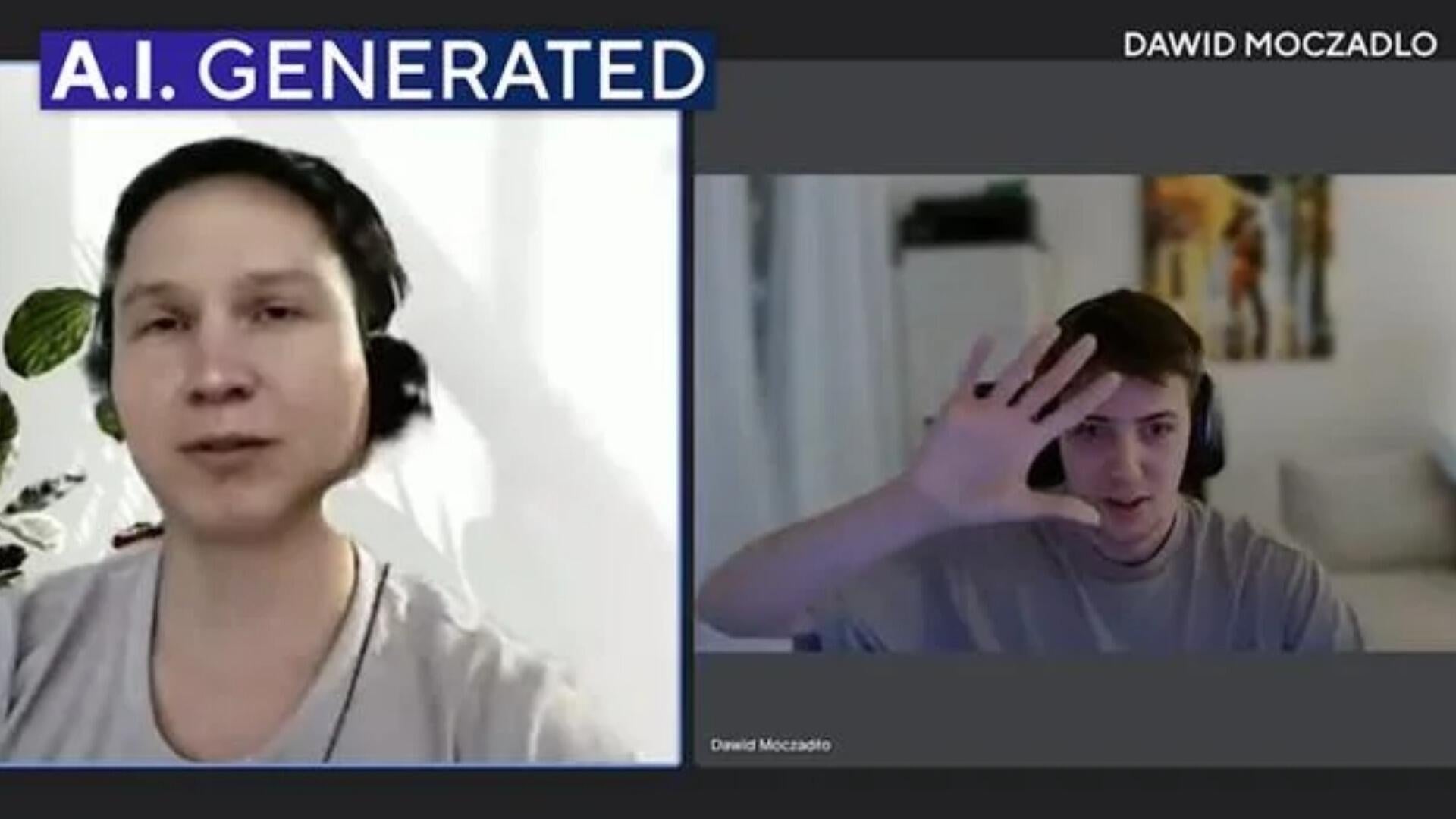
1. Create Fake Recruiter Profiles on Trusted Platforms: Hackers use AI-generated photos and details to build convincing recruiter identities on LinkedIn and Telegram, often impersonating staff from reputable crypto firms like Coinbase or Uniswap.
-
2. Send Credible Job Offers to Crypto Professionals: The attackers reach out to targets with personalized messages, offering lucrative positions at well-known companies. These offers often mimic real job postings, increasing their believability.
-

3. Request Malicious Skills Assessments or Interviews: Victims are asked to complete coding tests or participate in video interviews. These assessments require downloading files or visiting specific websites, which secretly install malware designed to steal credentials and crypto wallet access.
-

4. Deploy Phishing Emails and Malware: Hackers send phishing emails or direct messages containing malicious links or attachments. Opening these allows malware—such as COVERTCATCH—to infiltrate devices, compromise private keys, and access digital assets.
-

5. Steal Credentials and Drain Crypto Accounts: Once malware is installed, it harvests login details and private keys, enabling hackers to access and empty wallets on major platforms. In 2025 alone, North Korean actors were linked to the $1.5 billion ByBit hack, contributing to over $2.17 billion stolen in crypto this year.
Hackers often ask candidates to complete coding tests or participate in video interviews requiring downloads of seemingly innocuous software. Once installed, this malware can silently compromise wallets or siphon off sensitive credentials, sometimes going undetected until substantial losses occur. In one recent case cited by Cointelegraph, applicants were asked to download a custom test environment that secretly harvested private keys from their devices.
Why New Crypto Workers Are Especially Vulnerable
If you’re new to the industry or transitioning from traditional finance or tech roles, you may not yet be attuned to these specific threats. The onboarding process for many crypto jobs is remote-first and fast-paced, a combination that creates fertile ground for attackers using social engineering tactics.
The stakes couldn’t be higher: with over $2.17 billion stolen in crypto so far in 2025, including a record-breaking $1.5 billion heist according to Chainalysis’ latest update (source), even one misstep can have devastating consequences for your portfolio and reputation.
Common Red Flags in Crypto Recruitment Scams
- Poor grammar or unusual communication times: Professional recruiters rarely send messages at odd hours or with language errors.
- Requests for private keys or wallet access: No legitimate employer will ever ask for this information during recruitment.
- Unsolicited attachments or links: Treat all unexpected files as potentially hazardous, even if they appear work-related.
- Lack of verifiable company details: Always cross-check recruiter profiles against official company channels before proceeding further.
While these scams can be unsettling, there are practical steps you can take to defend yourself and your assets. The crypto industry’s decentralized and often anonymous nature means that once funds are lost, recovery is virtually impossible. That’s why prevention and vigilance are your best allies.
Proactive Security: How to Protect Yourself from Crypto Phishing Recruitment
Start by treating every unsolicited job offer with a healthy dose of skepticism, no matter how enticing the opportunity or how reputable the company appears. Here’s what you should do if approached by a recruiter in the crypto space:
Always initiate contact with companies through their official website or verified social media accounts before engaging further. If you’re asked to download software or share sensitive information as part of an application process, pause and consult trusted industry peers or online communities first.
Staying Ahead: The Evolving Nature of Crypto Scams
North Korean hackers are not just relying on old tricks. The use of AI-generated recruiter profiles has made it harder than ever to spot fakes at a glance. Some attackers even target developers directly via technical forums and Telegram channels, exploiting the collaborative spirit that’s so essential to blockchain innovation (Decrypt). As machine learning tools evolve, expect these scams to become more personalized and convincing.
Tip: If a recruiter insists on using unofficial communication channels or resists verification, treat this as an immediate red flag.
Bitcoin Maintains Position Above $100,000 Despite Security Threats
The resilience of Bitcoin, now holding steady at $110,786.00: shows that market confidence remains high even as security risks escalate. However, this price level also makes the ecosystem an especially attractive target for cybercriminals. As more capital flows into digital assets, both individual investors and companies must prioritize robust onboarding safety measures.
If you’ve fallen victim to a scam or suspect malicious activity during a recruitment process, report it immediately to both the affected platform (such as LinkedIn or Telegram) and relevant authorities. Sharing your experience within trusted crypto communities can help others avoid similar pitfalls.
Resources for Beginner Crypto Security
- Stay Safe from Crypto Fraud: Tips and Best Practices for 2024 (Unit21)
- 2025 Crypto Crime Mid-Year Update (Chainalysis)
- North Korean Hackers Target Crypto Experts (BleepingComputer)
The bottom line? Crypto onboarding safety is not just about understanding blockchains or wallets, it’s about developing strong digital habits and recognizing that trust is earned, not given freely online. As North Korean hackers innovate their tactics in 2025 and beyond, staying informed is your best defense against their relentless campaigns targeting both new investors and seasoned professionals alike.



