In October 2025, the decentralized trading platform Hyperliquid became the focal point of crypto security discussions after a staggering $21 million was siphoned from a user’s account. The breach was traced to a private key leak, a stark reminder that even in a market where Bitcoin has surged past $100,000 and DeFi protocols are more sophisticated than ever, the basics of digital asset protection remain paramount. As cyber threats evolve, so must your defense strategies, especially if you’re new to crypto or looking to level up your security posture.

What the Hyperliquid Hack Revealed About Modern Crypto Threats
The Hyperliquid incident is not an isolated event. In just the first half of 2025, access control failures have led to over $1.6 billion in crypto losses (Blockchain Council). These failures include everything from social engineering attacks to simple lapses in private key storage discipline. The Hyperliquid hack stands out for one crucial reason: it was enabled by a private key leak, a preventable mistake with devastating consequences.
For anyone onboarding into crypto or managing significant holdings, this event underscores four critical lessons. Here’s how you can protect yourself against 2025’s most prevalent and costly security risks:
Actionable Security Tips for Protecting Your Crypto in 2025
Top Crypto Security Tips for 2025
-

Never Store Private Keys Online or in Cloud ServicesStoring private keys in email, cloud storage (like Google Drive or Dropbox), or messaging apps exposes them to hacks and leaks, as seen in the $21M Hyperliquid exploit. Always keep private keys offline and never share them with anyone.
-
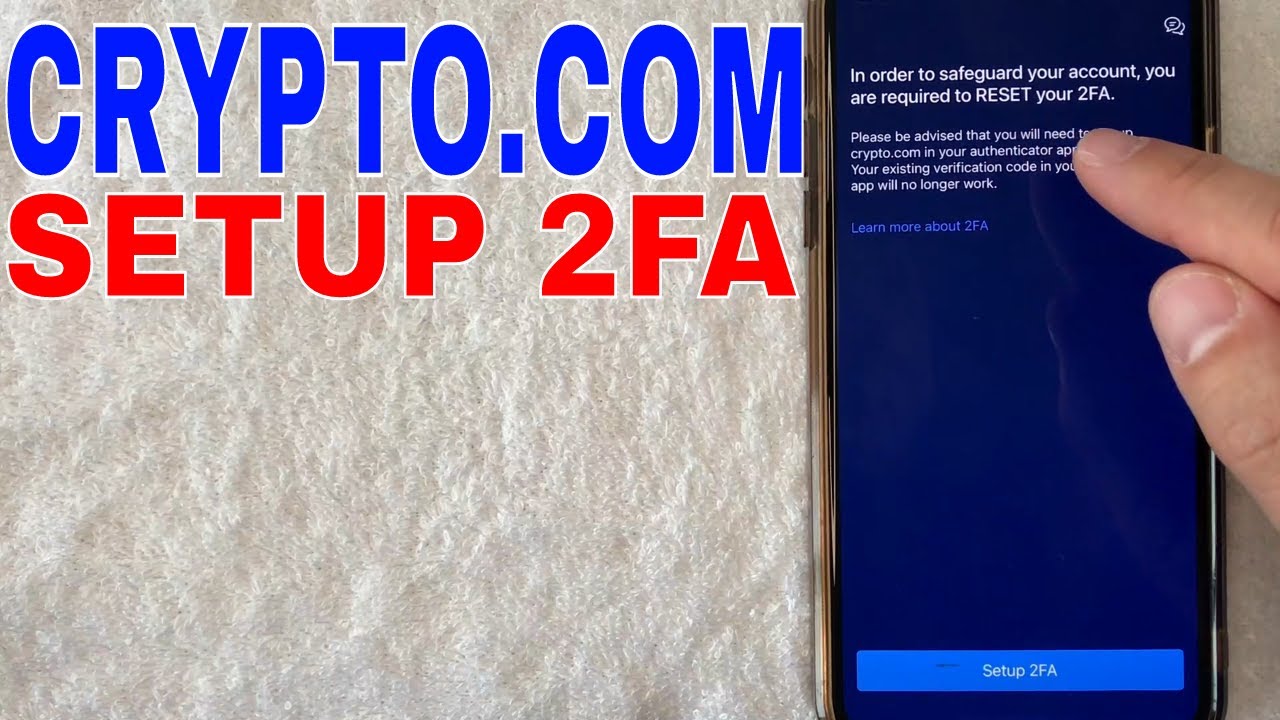
Enable and Regularly Update Two-Factor Authentication (2FA) on All Crypto AccountsProtect your exchange and wallet logins by enabling 2FA using app-based authenticators (like Google Authenticator or Authy), not SMS. Regularly update your authentication methods to guard against evolving access control attacks.
-
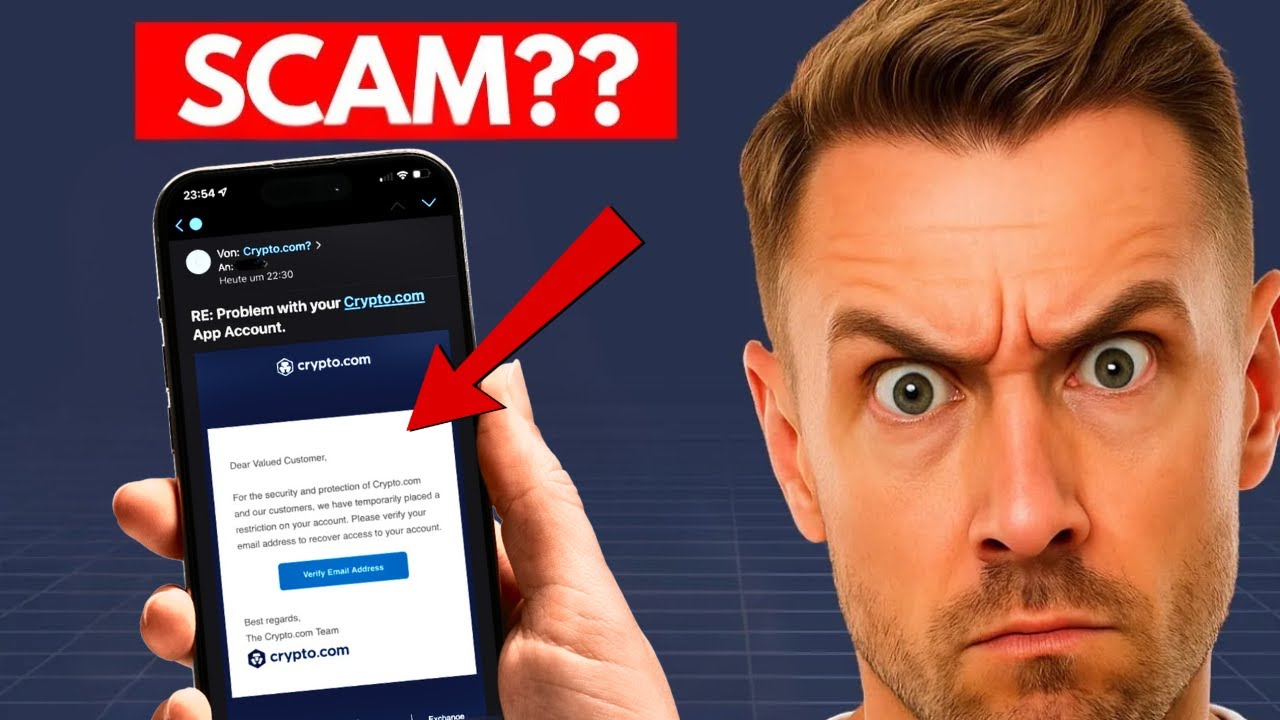
Be Vigilant Against Phishing Scams and Always Verify URLs and Sender IdentitiesPhishing attacks are increasingly sophisticated in 2025. Double-check website URLs, beware of fake support emails, and never click on suspicious links. Bookmark official sites and use password managers to avoid typosquatting traps.
1. Never Store Private Keys Online or in Cloud Services
The single most important takeaway from the Hyperliquid exploit is this: never store your private keys or seed phrases online. Cloud drives, email attachments, and note-taking apps are all vulnerable to hacks and unauthorized access. Attackers frequently scan these services for unencrypted keys. In the Hyperliquid case, once the attacker obtained the private key, they had full control over the victim’s assets, no amount of blockchain-level security could help.
Best practice: Write down your seed phrase on paper and store it in a secure location. For extra protection, consider splitting it between trusted locations or using specialized steel backup devices designed for fire and water resistance.
2. Enable and Regularly Update Two-Factor Authentication (2FA) on All Crypto Accounts
Access control failures are rampant in 2025, with sophisticated phishing and impersonation attacks targeting both centralized and decentralized platforms. Enabling two-factor authentication (2FA) is non-negotiable for every exchange, wallet, and DeFi app you use. Even better: use app-based authenticators (like Google Authenticator or Authy) instead of SMS-based 2FA, which can be bypassed via SIM swap attacks.
Regularly update your 2FA settings and backup codes. If a platform offers multi-factor authentication (such as requiring both an app code and biometric verification), opt in for maximum protection.
Market Context: Why Security Matters More Than Ever
The stakes are higher in 2025. With Bitcoin’s price maintaining levels above $100,000 and high-profile hacks like Bybit’s $1.5 billion exploit still fresh in memory (AP News), attackers are more motivated than ever. For new users especially, robust onboarding into crypto security is essential, not just for peace of mind but for real financial survival.
3. Use Hardware Wallets for Large or Long-Term Holdings
For anyone holding significant amounts of cryptocurrency, hardware wallets are the gold standard for safeguarding assets. Unlike software wallets connected to the internet, hardware wallets store your private keys offline, making them immune to online hacks and malware attacks. In the wake of the Hyperliquid incident, this step is not optional, it’s foundational.
When selecting a hardware wallet, opt for reputable brands with a proven track record and transparent security audits. Always purchase directly from the manufacturer or an authorized reseller to avoid supply chain tampering. For large or long-term holdings, consider using multiple hardware wallets with different backup strategies for added redundancy.
4. Be Vigilant Against Phishing Scams and Always Verify URLs and Sender Identities
Phishing attacks in 2025 have reached new levels of sophistication. Attackers craft convincing emails, fake support chats, and even clone entire websites to steal credentials and private keys. The Hyperliquid hack highlighted how a single lapse in vigilance, such as clicking a malicious link or trusting an imposter, can result in catastrophic loss.
Always double-check URLs before logging into any crypto platform. Bookmark official sites and scrutinize email sender addresses for subtle misspellings or odd domains. Never share sensitive information over chat or email, even if the request appears to come from official support staff. When in doubt, contact platforms through verified channels.
Adapting Your Strategy: From Reactive to Proactive Security
The lessons from Hyperliquid’s $21 million breach extend far beyond one unlucky trader, they’re a call to action for everyone in crypto. With access control failures causing billions in losses (Blockchain Council) and phishing campaigns more advanced than ever (Analytics Insight), it’s clear that security is not just about technology but also behavior.
Stay informed by following trusted sources on social media, participating in community discussions, and keeping up with the latest threat intelligence reports. Proactive education is your best defense against evolving scams and exploits.
Summary Table: 2025’s Top Crypto Security Tips at a Glance
Effectiveness of Key Crypto Security Tips Against Major Threat Vectors (2025)
| Security Tip | Phishing Attacks | Key Theft/Private Key Leaks | Exchange Hacks |
|---|---|---|---|
| Never Store Private Keys Online or in Cloud Services | Moderately Effective | Highly Effective | Not Effective |
| Enable and Regularly Update Two-Factor Authentication (2FA) on All Crypto Accounts | Highly Effective | Moderately Effective | Moderately Effective |
| Use Hardware Wallets for Large or Long-Term Holdings | Moderately Effective | Highly Effective | Not Effective |
| Be Vigilant Against Phishing Scams and Always Verify URLs and Sender Identities | Highly Effective | Moderately Effective | Not Effective |
The Hyperliquid hack was preventable, and so are most losses in today’s market if you follow these prioritized tips:
- Never store private keys online or in cloud services
- Enable and regularly update 2FA on all accounts
- Use hardware wallets for significant holdings
- Be vigilant against phishing scams, always verify before you trust
With Bitcoin trading above $100,000 and DeFi platforms surging in popularity, the risks are real but manageable for those who plan their security as methodically as they plan their trades.




