How Bitcoin Depot’s ATM Expansion and Crypto ATM Scams Impact Onboarding: What New Users Need to Know in 2025
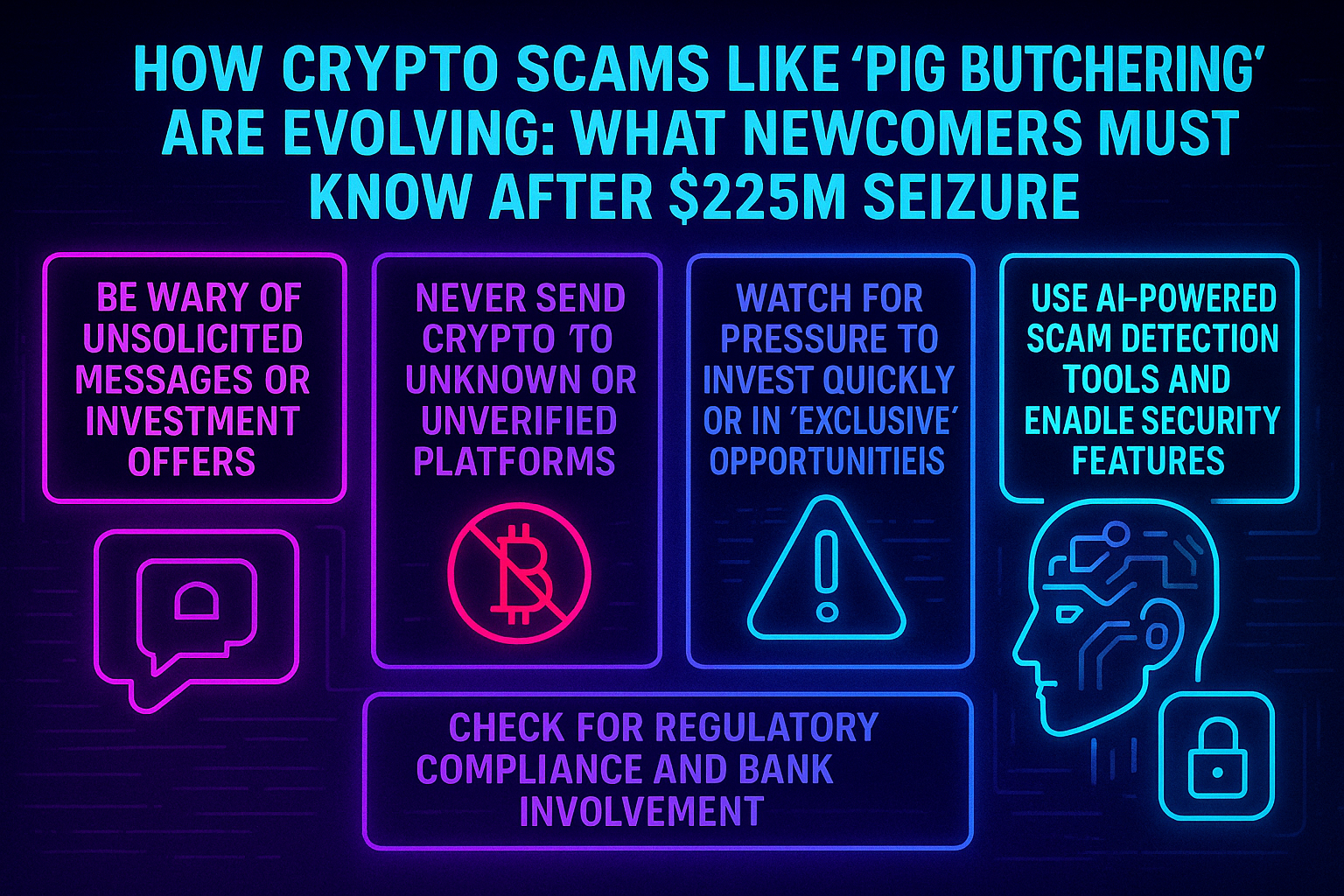
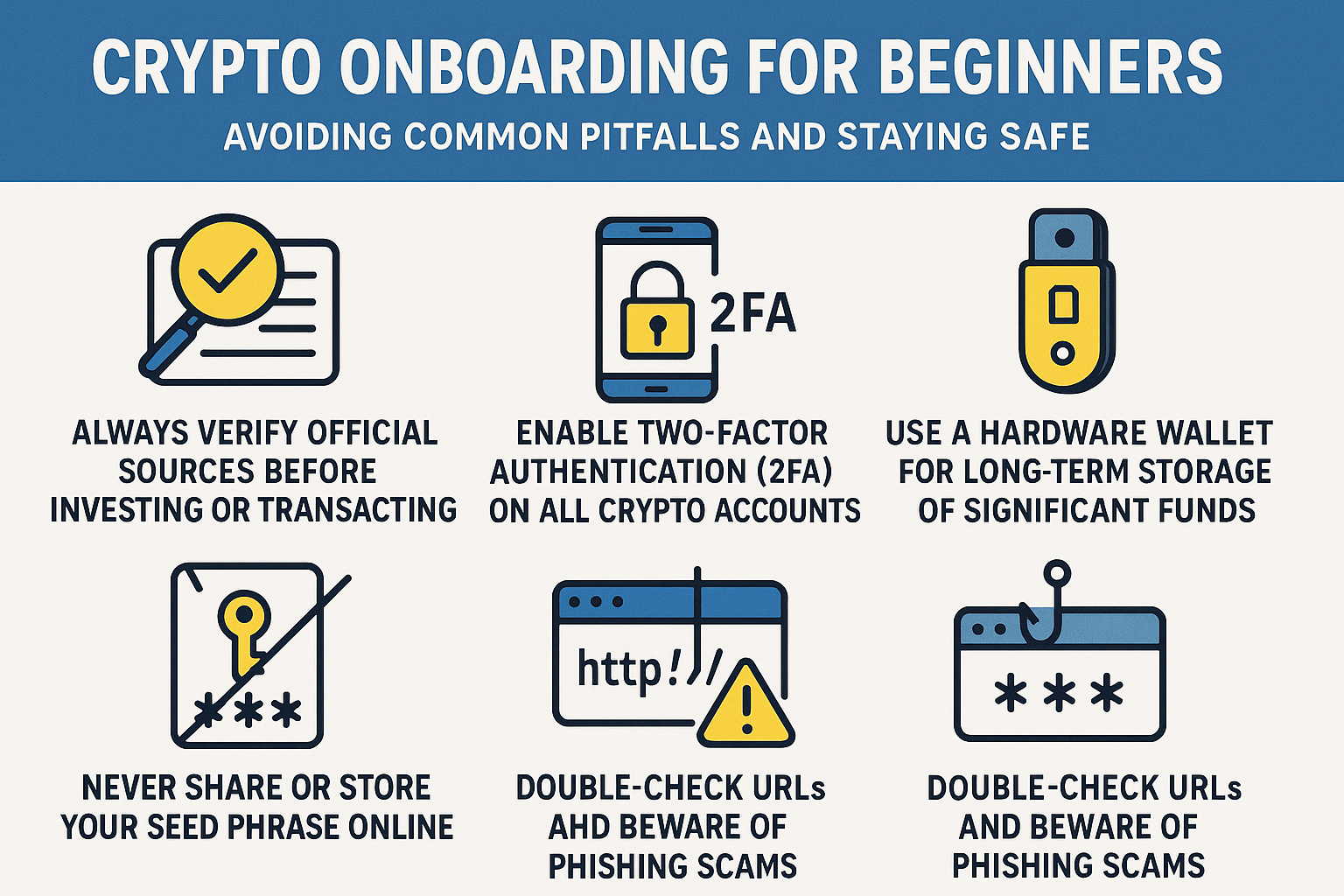
Bitcoin Depot’s ATM network is everywhere in 2025, and with Bitcoin trading above $122,540.00, crypto feels more mainstream than ever. But as the orange B lights up more street corners,…