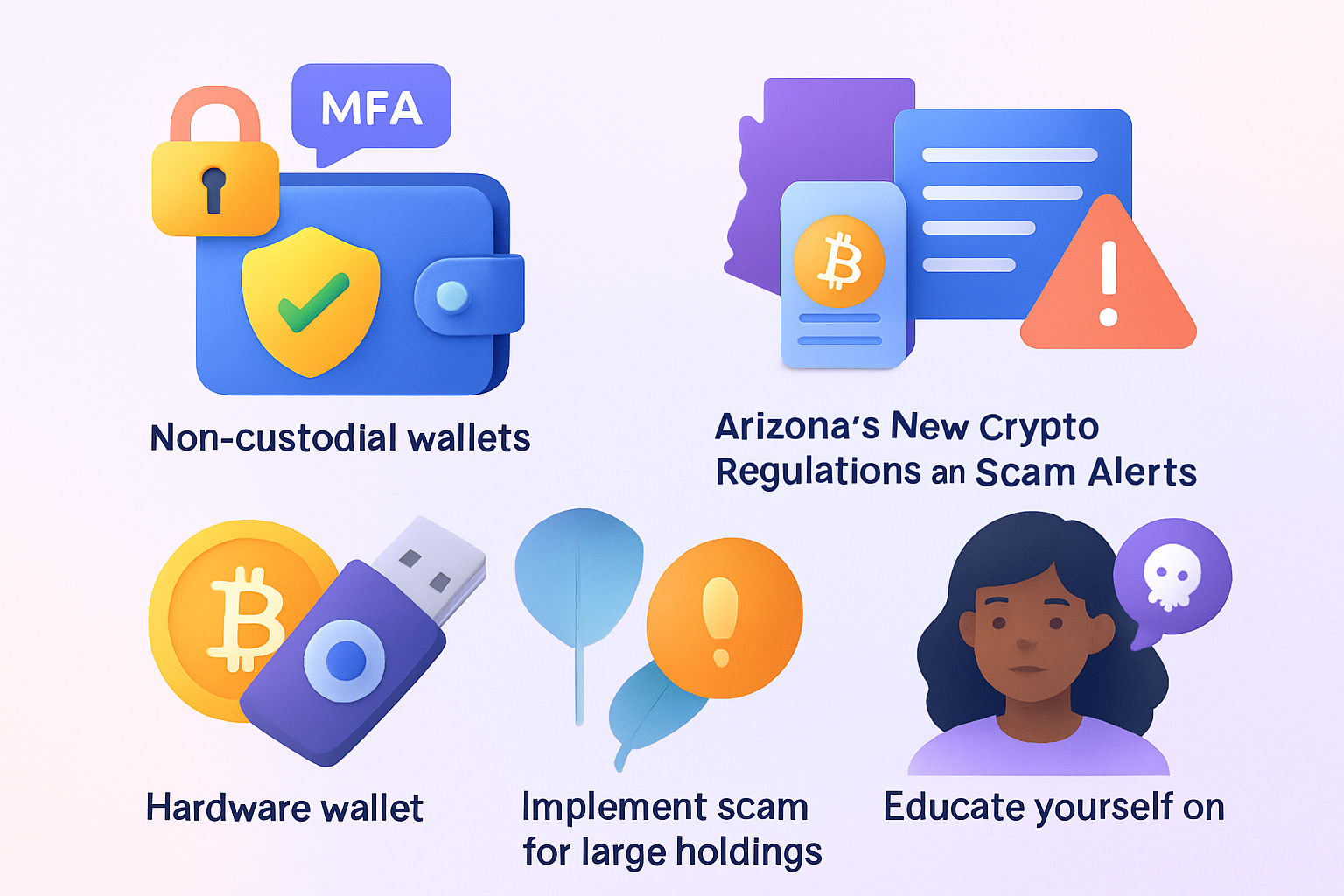
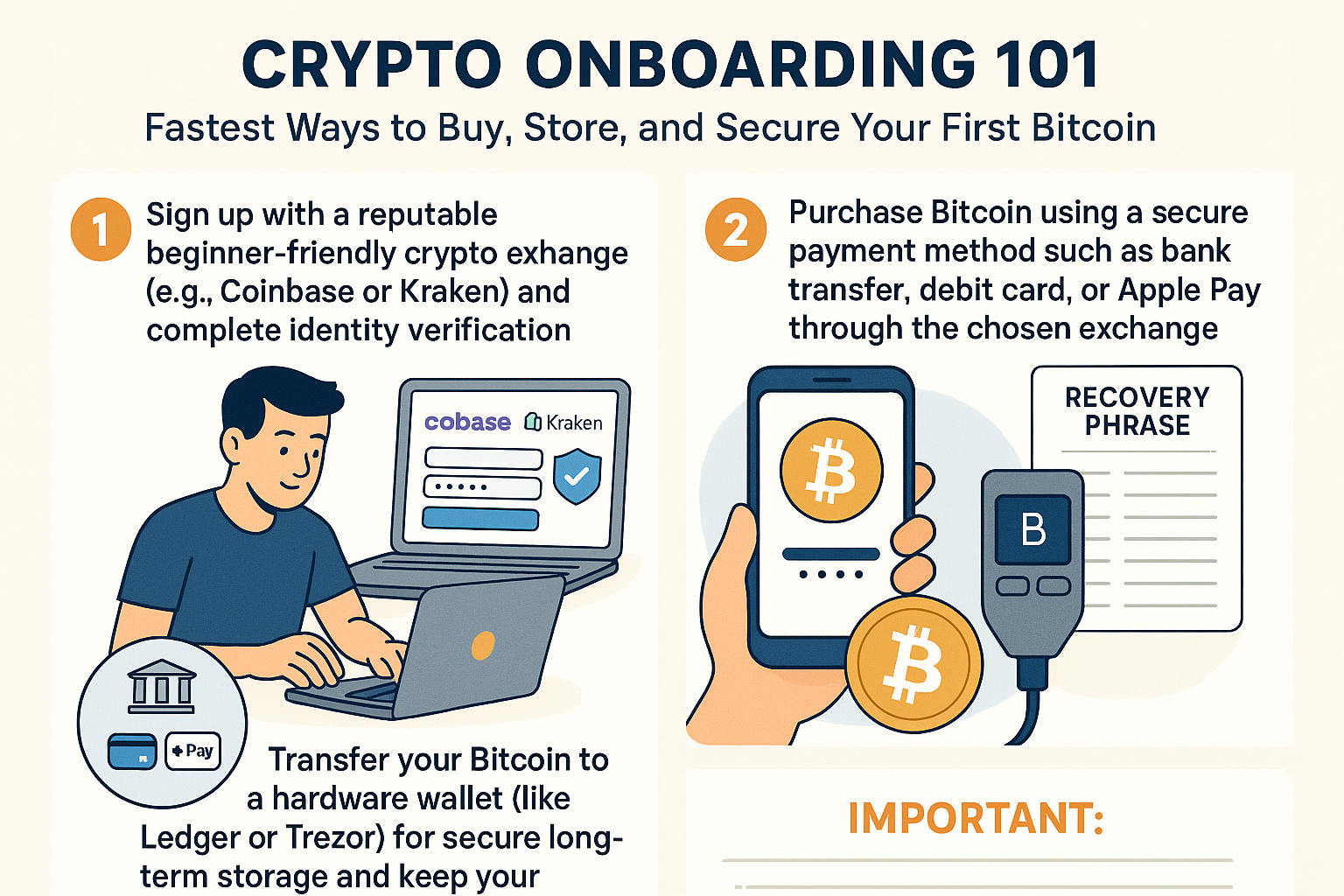
Crypto Self-Custody in 2025: Lessons from Recent Exchange Failures and Web3 Security Trends
In 2025, the world of cryptocurrency has reached a new level of maturity, but with it comes a deeper awareness of risk. The past year alone has seen Bitcoin maintain…